Secure Software Life Cycle
FAQ
SDLC (Software Development Life Cycle) is a structured process used by software development teams to design, develop, test, and deploy high-quality software. It consists of several phases that outline the steps developers take to create software:
- Planning
- Analysis
- Design
- Development
- Testing
- Deployment
- Maintenance
The SDLC's purpose is to:
- Ensure efficient and effective software development
- Meet stakeholder needs
- Provide a framework for managing the entire process from idea to delivery
- Produce reliable, maintainable, and scalable software
The first step of the SDLC is the planning phase. During this crucial stage:
- The development team collaborates with stakeholders to understand requirements and goals
- The project scope is determined
- Deliverables are defined
- A project plan outlining the timeline and required resources is created
This phase sets the foundation for the entire development process, ensuring alignment with stakeholder needs. Deliverables may include:
- Project charter
- Requirements document
- Feasibility study
- Project plan
- Risk management plan
The Secure Software Development Life Cycle (SSDLC) is an extension of the traditional SDLC that incorporates security practices and considerations at every phase of the development process. It aims to create secure and robust software systems by:
- Integrating security into each SDLC stage
- Identifying and addressing security risks and vulnerabilities throughout development
- Preventing security issues rather than patching them post-deployment
SSDLC practices include:
- Threat modeling
- Code review
- Security testing
- Security training for developers
Benefits of SSDLC:
- Time and resource savings
- Reduced likelihood of costly security breaches
- Meeting stakeholder security requirements
- Protection against potential security threats
SDLC and Scrum are distinct approaches to software development:
- Methodology:
- SDLC: Linear, step-by-step approach with sequential phases
- Scrum: Iterative and incremental approach with small, iterative cycles
- Requirements:
- SDLC: Defined at the beginning and remain relatively fixed
- Scrum: Continually refined and prioritized, subject to change
- Roles:
- SDLC: Fixed roles with clear lines of responsibility
- Scrum: Collaborative roles with shared responsibility
- Planning:
- SDLC: Comprehensive planning at project start
- Scrum: Flexible planning at the beginning of each sprint
- Delivery:
- SDLC: Final product delivered after all phases are completed
- Scrum: Potentially releasable increment delivered at the end of each sprint
These differences highlight the contrasting approaches of SDLC's structured, linear process and Scrum's flexible, iterative methodology.
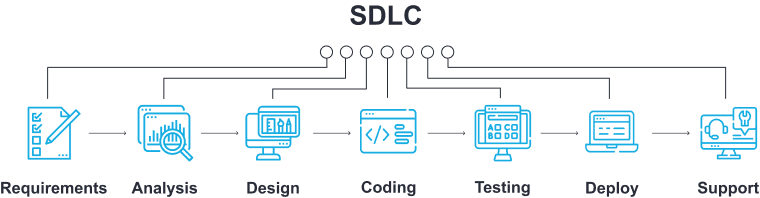
The number of steps in the Software Development Life Cycle (SDLC) can vary depending on the methodology or framework used. However, the typical SDLC process consists of six phases:
- Planning: In this phase, the team defines the project's scope, objectives, and requirements, and creates a project plan and schedule.
- Analysis: The team conducts a detailed analysis of the project requirements and gathers information to create a software design specification.
- Design: The team develops the software architecture, design, and specifications based on the analysis conducted in the previous phase.
- Implementation: The team begins coding and developing the software according to the specifications created in the design phase.
- Testing: This phase involves verifying that the software functions correctly and meets the specified requirements.
- Maintenance: The final phase involves ongoing maintenance and support of the software after deployment.
These phases may overlap, and iterations or repetitions within each phase can occur. While the number and names of the phases may vary, the overall purpose of each phase is to ensure efficient and effective software development that meets stakeholders' needs.
The implementation phase of the SDLC provides the completed system. This phase involves the actual coding and development of the software based on the specifications created in the design phase. It includes several sub-phases such as coding, testing, debugging, and integration.
During implementation, the software development team converts design documents into working software. They write code, create databases, and build user interfaces, among other activities. Once coding is completed, the team conducts various tests to ensure the software functions correctly, meets specified requirements, and is free of errors and bugs.
At the end of the implementation phase, the completed system is delivered to the testing team for further evaluation. Once the software passes all tests and receives approval, it can be deployed for end-user use. However, the maintenance phase, which follows deployment, is also critical, as it involves ongoing support and updates to ensure the software continues to meet users' needs.
The Software Development Life Cycle (SDLC) is a process used by software development teams to create software systems. While the exact steps can vary depending on the methodology or framework used, the following outlines the general phases involved:
- Planning: Define the project's scope, objectives, and requirements; create a project plan and schedule.
- Analysis: Conduct a detailed analysis of project requirements and gather information to create a software design specification.
- Design: Develop the software architecture, design, and specifications based on the analysis from the previous phase.
- Implementation: Code and develop the software based on the design specifications. This phase includes coding, testing, debugging, and integration.
- Testing: Verify that the software functions correctly and meets specified requirements. Testing can include unit testing, integration testing, system testing, and acceptance testing.
- Deployment: Release the software and make it available to end-users.
- Maintenance: Provide ongoing support and maintenance after deployment, including bug fixes, updates, and upgrades.