Social engineering simulation
Effective and Efficient Training to Recognize and Prevent Phishing Attacks
Phishing simulation is a method of training and testing employees to recognize and prevent phishing attacks aimed at unauthorized access to confidential information and other security breaches.
The most effective approach combines phishing simulation with penetration testing and awareness training.
Our Teaching Strategies for Phishing Detection and Prevention
We have developed unique training methods and scenarios, tailored to the specific needs of your industry, aiming to educate your employees to recognize and prevent social engineering threats.
The key features of our service are:
- Customized Approach. We understand that every business is unique. Our simulations are individually crafted for each client, ensuring maximum relevance and effectiveness. This approach allows us to personalize scenarios, considering the unique characteristics of your industry and business processes.
- Realistic Simulations. We offer not only training exercises but also realistic simulations, using emails, websites, unique executable attachments that can bypass your anti-malware, and other phishing means and methods. The simulation encompasses all users with email addresses in your organization who are obliged to follow your information security protocols. All this ensures a high degree of practical experience necessary to combat phishing threats effectively.
- Assessment and Training. We provide detailed reports containing results that can be used for personalized employee training, addressing weaknesses, and enhancing cybersecurity levels.
What makes our phishing simulation services special?
We apply social engineering with advanced targeting. In addition to typical automated phishing simulations, we offer manual modeling of targeted attacks (spear phishing), as close as possible to the real actions of attackers.
Unlike mass automated simulations like PhishingBox, the services of modeling targeted sociotechnical attacks are rare on the market. Ordering them from us, you can be sure that you get the highest level of quality and readiness for real attacks of real criminals: financial system hackers, extortionists, raiders, industrial spies or APT agents, who have been preparing for an attack for months, and not just small fraudsters and other spammers, which can be protected from by an ordinary mail gateway or anti-spam.
More about our features and quality system.
Training to Prevent Advanced Phishing Techniques
Our training focuses on advanced forms of phishing, including “spear phishing” and “whaling.” Unlike mass phishing, these tactics involve cybercriminals targeting specific employees or top executives of companies.
Spear Phishing. In this attack type, perpetrators identify specific targets in the company and create highly individualized deceptive scenarios.
Our simulations of spear phishing involve various tactics, such as communication via LinkedIn and other social networks, simulating messages from colleagues, clients, or partners to closely replicate real attack scenarios in a credible way. This form of training prepares individuals to recognize and thwart these sophisticated phishing attempts.
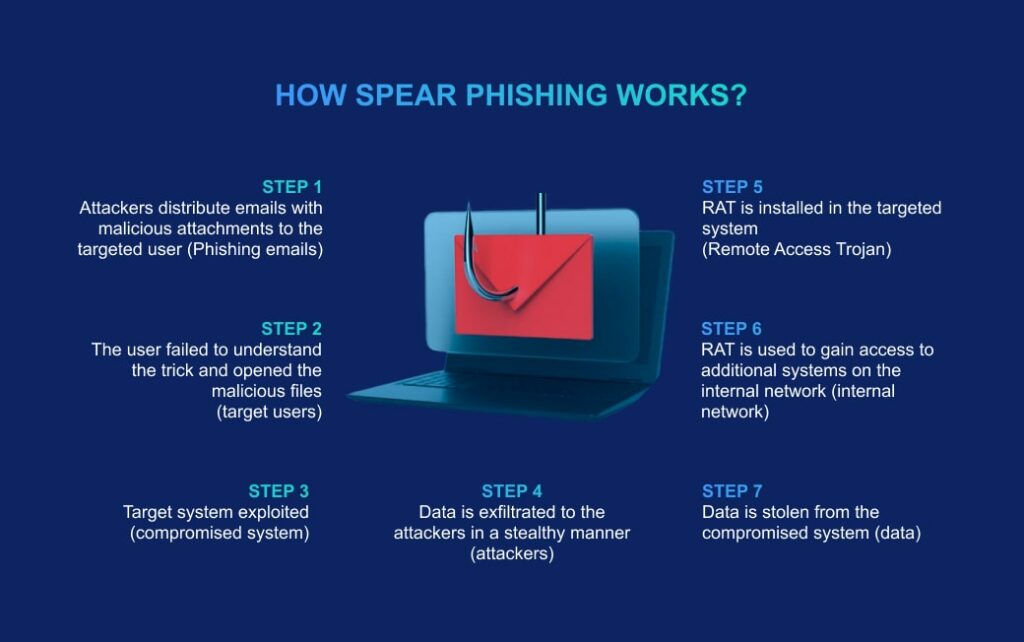
Whaling. Whaling phishing targets the key executives and individuals who make strategic and other critical decisions.
During simulations, we enact methods and scenarios involving offline correspondence, the imitation of requests from key clients, partners, investors, government entities, etc., aiming to assess how much the top executives are ready for such sophisticated attacks
Our training not only identifies the vulnerabilities in your defense against such attacks but also focuses on strategies and methods specific to each type of phishing. By doing so, we enhance awareness and readiness among top-level decision-makers to counter these particular threats effectively.
Phishing Prevention Skills: Essential Training for a Successful Business
By investing in a phishing simulation service, you significantly enhance your company’s defense against cyberattacks and acquire numerous advantages:

Increased Employee Awareness
The weakest link in cybersecurity systems is often human. Training employees to recognize phishing helps prevent potential incidents related to data breaches, business interruptions, and other negative consequences.

Reduction in Successful Phishing Attacks
Our clients have observed that after utilizing our service, the average percentage of correctly identified phishing emails by employees increased from 70% to 95%. Additionally, the number of successful phishing attacks against our clients is 4-5 times smaller.

Cultivation of Cybersecurity Culture
Regular training and testing help maintain a high level of awareness about cyber threats, promote the development of safe Internet behavior habits, and reduce the risk of damage from many types of incidents, beyond mere information leaks associated with phishing.

Compliance with Regulatory Requirements
In some industries and jurisdictions, conducting cybersecurity training and tests, including social engineering prevention, is a mandatory requirement for ensuring compliance with regulatory standards.
Free consultationCheck out our additional services and business cases. Send the form below to request the social engineering simulation service. Get a free consultation.
