SOC 2 implementation
What is evaluated during the SOC 2 audit?
Physical, IT, and other hardware such as mobile devices.
Applications and IT system software that supports application programs, such as OS and utilities.
All personnel involved in the organization’s operations.
All automated and manual procedures.
Transmission streams, files, databases, tables, and output used or processed by your organization.
Deliverables of SOC 2 implementation
SOC 2 implementation results in a report based on AICPA SSAE and Attestation Standards. H-X Technologies provides audit reports specifically designed for technology service providers, SaaS companies, and organizations that store data in the cloud.
Types of SOC 2 report
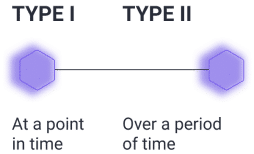
Type I – A Type 1 report is a snapshot: at the time the report was compiled, the organization had the appropriate controls that made it compliant with the SOC 2 standards. The report is a starting point for building the SOC 2 Type 2 compliance.
Type II – A Type 2 report is more difficult to attain, but it also assures much stronger compliance. The organization must demonstrate adherence to the controls and policies for a period of time, and that usually requires a degree of automation and a long-term commitment.
We will help you choose which type of report is right for you.
Why are we the best?
We offer SOC 2 solutions that are flexibly customized to your budget and needs.
From affordable consultative audits, collaborative implementations and control evaluation reports, to Letters of Opinion and attestations by our partners, leading CPA firms, including the Big Four leaders. In any of these options, we reduce your costs by streamlining your implementation processes while maintaining compliance with strict SOC 2 standards.
You won’t find this kind of flexibility and breadth of service options in a single package from our GRC competitors or CPAs themselves.
Service summary
| ⏳ Duration of project | On average, from 5 to 8 months from scratch. Faster if you manage your security. Longer if your infrastructure and processes are complex. |
| 🎁 Can it be free or have a trial period? | Free consultation and initial analysis of business requirements. Use our virtual expert. |
| 💼 What type of business needs it? | SaaS and other technology companies, finance, healthcare, and any service company handling sensitive data. |
| 💡 When is this service needed? | When you want to demonstrate your commitment to information security, especially in the USA. |
| 📈 Your profit | Improved customer confidence, reduced data security risks, new opportunities for partnerships, avoided potential fines and legal fees. |
| ⚙️ Our methods and tools | Policy and procedure development, risk assessment, access control reviews, vulnerability assessments, penetration testing, security awareness training, etc. |
| 📑 Deliverables | Final audit report describing compliance with the relevant trust services criteria, and areas for improvement. |
Check out our additional services and business cases. Send the form below to request the SOC 2 compliance. Get a free consultation.
FAQ
The cost of implementing SOC2 varies significantly based on several factors:
- Organization size
- System and process complexity
- Assessment scope
- Existing security program maturity
- Experience of the assessment team
Key cost components:
- External consultants or auditors
- Security tools and technologies
- Internal training and awareness programs
- Policy and process changes
Note:
- Costs can be spread out by implementing SOC2 in phases
- Consider SOC2 implementation as a long-term investment in security posture
Benefits include increased customer trust, improved risk management, and better regulatory compliance.
Organizations implement SOC2 for various reasons:
- Compliance: Meet industry standards and customer requirements
- Risk Management: Identify and mitigate security risks
- Competitive Advantage: Differentiate from competitors
- Process Improvement: Enhance security and privacy processes
- Customer Trust: Demonstrate commitment to data protection
SOC2 implementation can lead to improved security posture, increased customer loyalty, and better overall business performance.
General steps for SOC2 implementation:
- Determine Scope: Identify systems, processes, and data for assessment
- Conduct Risk Assessment: Identify and prioritize risks
- Develop Policies and Procedures: Align with SOC2 requirements
- Implement Controls: Address identified risks
- Conduct Testing: Ensure control effectiveness
- Engage Independent Auditor: Perform SOC2 assessment
- Address Issues: Improve controls and processes as needed
- Maintain Compliance: Conduct regular assessments and updates
Note: The specific steps may vary based on organizational factors.
A SOC2 report is the outcome of a SOC2 audit or assessment, providing an independent evaluation of an organization's compliance with SOC2 guidelines and controls.
Key components of a SOC2 report:
- System and Process Description:
- Detailed overview of the organization's systems and processes
- Description of implemented security, availability, confidentiality, and integrity controls
- Auditor's Opinion:
- Independent assessment of control effectiveness
- May include a clean opinion or identify areas for improvement
SOC2 reports serve as valuable documentation of an organization's commitment to security and data protection, often used to build trust with customers and partners.
A SOC2 report's validity period is determined by the organization and its stakeholders. The American Institute of Certified Public Accountants (AICPA), responsible for creating and maintaining SOC2 standards, does not prescribe a specific validity period.
Typically, SOC2 reports cover a period of six months to a year, depending on the organization's needs and stakeholder requirements. Many organizations conduct annual SOC2 assessments and issue new reports each year.
It's important to note that while a SOC2 report may be valid for a certain period, it doesn't guarantee the ongoing effectiveness of an organization's controls. Organizations must continually monitor and update their controls to ensure ongoing compliance with SOC2 standards and address any changes or new risks that may arise.
Stakeholders may request a more recent SOC2 report than the organization's standard assessment cycle, particularly if significant changes have occurred in the organization's systems or processes. Therefore, organizations should be prepared to conduct assessments and issue new SOC2 reports as needed to meet stakeholder requirements.
To obtain a SOC2 report, an organization must undergo a SOC2 audit or assessment by an independent auditor. Here are the general steps:
- Determine the scope: Identify the systems, processes, and data to be included in the SOC2 assessment. This helps define the scope and ensure all relevant areas are covered.
- Conduct a risk assessment: Identify risks to the organization's systems, data, and processes. This helps prioritize areas that need attention and determine appropriate controls to implement.
- Develop policies and procedures: Create and implement policies and procedures that address the risks identified in the assessment. These policies should align with SOC2 requirements and be reviewed and updated regularly.
- Implement controls: Put in place the controls identified in the risk assessment and policies. These controls should be designed to address identified risks and tested to ensure their effectiveness.
- Engage an independent auditor: Hire an independent auditor to perform the SOC2 assessment. The auditor will evaluate the organization's controls and processes against SOC2 requirements and provide a report on their findings.
- Address any issues: Resolve any issues identified during the assessment and make necessary improvements to controls and processes.
- Obtain SOC2 report: After completing the assessment, the auditor will issue a SOC2 report that provides an independent assessment of the organization's compliance with SOC2 requirements.
The cost of a SOC2 report can vary widely depending on several factors, including:
- Scope of assessment: More complex assessments covering multiple systems, processes, and data types will be more time-consuming and costly.
- Type of report: Type 2 reports are generally more expensive than Type 1 reports because they cover a longer period and require more extensive testing of controls.
- Auditor expertise: More experienced auditors may charge higher fees for their services.
- Preparation and remediation costs: Organizations may need to invest in additional controls or remediation efforts to address issues identified during the assessment.
- Additional services: Some organizations may require supplementary services such as penetration testing, vulnerability scanning, or policy development, which can increase the overall cost.
Given the numerous variables involved, it's challenging to provide a specific cost estimate for a SOC2 report. Organizations should consult with auditors and service providers to get accurate cost estimates based on their specific needs and circumstances.
Follow these steps to effectively review a SOC2 report:
- Understand the scope: Review the scope section to identify the systems, processes, and data included in the assessment.
- Determine the report type: Identify whether it's a Type 1 or Type 2 report. Type 1 assesses control design at a specific point, while Type 2 evaluates control effectiveness over a specified period.
- Review the auditor's opinion: Read the auditor's overall assessment of the organization's controls and processes.
- Examine control objectives: Review the control objectives section to understand the specific controls tested and their results.
- Analyze exceptions or deficiencies: If identified, review the section discussing these issues and their impact.
- Review complementary user entity controls (CUECs): Understand the user organization's responsibilities for maintaining their own controls.
- Assess management's assertion: Review the section where management asserts their compliance with SOC2 requirements.
- Consider additional information: Examine any other relevant information included in the report.
- Evaluate the report holistically: Determine whether the organization has met SOC2 requirements and if their controls are effective.
When reviewing a SOC2 report, focus on these key elements:
- Scope: Ensure it covers systems, processes, and data relevant to your organization.
- Report type: Determine if it's Type 1 or Type 2.
- Auditor's opinion: Assess the organization's compliance with SOC2 requirements and control effectiveness.
- Control objectives: Understand the specific controls tested and their results.
- Exceptions or deficiencies: Review any identified issues and their impact on the control environment.
- Complementary user entity controls (CUECs): Understand user organization responsibilities.
- Management's assertion: Review management's compliance statement.
- Report date: Ensure the report is current and relevant.
- Additional information: Consider any other pertinent details included.
- Remediation plans: Review plans to address any identified exceptions or deficiencies.
A SOC2 report is a compliance document that evaluates and reports on a service organization's controls related to security, availability, processing integrity, confidentiality, and privacy. The report typically includes:
- Scope and boundaries of the systems covered
- Description of the service organization's system
- Applicable trust services criteria
- Management's assertion of compliance
- Independent auditor's opinion
- Detailed description of controls and their effectiveness
- Test procedures performed by the auditor
- Results of control testing
- Any exceptions or deficiencies identified
- Complementary user entity controls (if applicable)
- Subservice organizations and their controls (if applicable)
- Management's response to identified issues (if any)
The SOC2 report provides detailed information on the design and effectiveness of these controls, which are crucial for maintaining customer and stakeholder trust and confidence. It also identifies any exceptions or deficiencies, helping the service organization improve its systems and processes.