Programmers’ mistake that endangered hundreds of millions of devices will take years to fix and cause billions in losses
In 2013, the authors of the popular open-source library Apache Log4j made a serious mistake in the log4j-core package for almost all versions of Log4j from 2.0-beta9 to 2.15.
This bug went unnoticed for more than 8 years. Alibaba Cloud researchers reported it to the Apache Foundation on 24 November 2021. Due to the release of the Log4j update on December 6, the vulnerability had to be disclosed on December 9.
The vulnerability was named Log4Shell and was coded CVE-2021-44228. Since it is so easy to be exploited remotely, this vulnerability received the highest base score of 10.0 in the overall CVSS vulnerability assessment system.
Hundreds of millions of computers and other devices around the world have been compromised. In particular, servers at Google, Apple, Twitter, Amazon Web Services, Cloudflare, Minecraft, and other major companies.
Apache’s official Twitter in June 2021 reported that the Martian Ingenuity helicopter contained Log4j. That tweet was later deleted, but nothing on the Internet disappears without a trace. The proof is in the web archive.
The vulnerability allows attackers to remotely send requests to execute arbitrary code, which gives them full control over the vulnerable system.
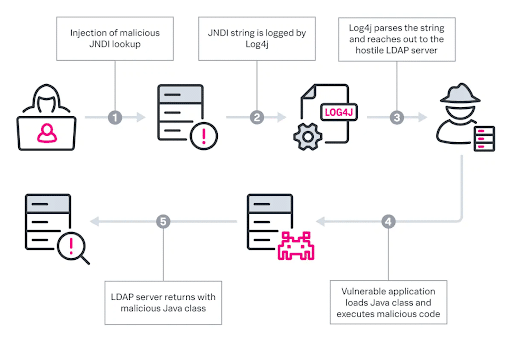
The most frequent targets of the hack are:
- cryptocurrency mining;
- ransomware;
- adding information to the server;
- stealing credentials.
A significant problem with the Log4Shell vulnerability appears to be the stealthiness of the attackers. In particular, government-sponsored groups involved in cyber warfare exploit this vulnerability in Advanced Persistent Threat (APT) mode. That is, attackers show no sign of intrusion, cover their tracks, and entrench themselves in compromised systems for years for spying and similar purposes. Unauthorised access will remain even after the vulnerability has been patched.
Another concern with the Log4Shell vulnerability is that it is difficult to fix on many devices. For example, on Smart TVs or surveillance cameras, because they were originally not designed for easy component updates. Therefore, it will likely take several years to fully fix this vulnerability.
Analysts are calling Log4Shell the largest and most critical computer vulnerability in history. The potential damage to the economy from this vulnerability is still difficult to estimate. This is likely to be in the billions of dollars. Given the number of vulnerable devices and the difficulty of “curing” them, Log4Shell can be safely compared to COVID-19 for the computer world.

A screenshot like this is familiar to anyone who has installed Java. The parody picture above exaggerates the real situation, since not all the 3 billion Java devices are vulnerable. However, there is some truth in every joke.
Given the unprecedented criticality of the Log4Shell vulnerability, and since we are aware of our social responsibility, H-X Technologies is ready, at short notice, to help protect and cleanse your systems from Log4Shell and other vulnerabilities, threats and attacks with our one-time penetration testing and incident investigation services.
If you need to protect not just individual systems, but your entire company and its infrastructure, our threat intelligence service can help you proactively anticipate such issues within your company, while our managed incident detection and response service can identify real attacks in time and properly remediate them.
If you’re developing your own software, our application security services can help you keep such vulnerabilities out of your software during the design and development phase. Our DevOps services through CI/CD pipelines and other methods help you mitigate the risks of vulnerabilities during the production phase of your applications and services.
Contact us today.
Subscribe to our Telegram channel so you do not miss new articles on our blog.
